Perfect Privacy VPN
8.96 ePositiv
- Swiss provider, completely in German! Answered all our questions about transparency completely and is considered "very trustworthy"!
- Dynamic cascades through "Neurorouting™"
- Effective filtering of "trackers" to track users not only for website content
- Connection to the TOR network
- Absolutely LOGFREE! + IPv6 support (security)
Negativ
- Higher price, but outstanding anonymity and technology
- Price corresponds to a premium provider
Table of Contents
Perfect-Privacy VPN Test Report: Maximum Swiss Anonymity and Privacy
Perfect-Privacy has been offered for more than 10 years, with special emphasis on secrecy and preservation of the user’s identity. Unparalleled high standards are set for security and protection against tracking, surveillance and exploration. The service belongs to the premium providers and is also designed for particularly security-conscious users.
Product name Perfect Privacy VPN Recommended areas of application Anonymous communicationAmazon Video (EN)VPN routerUse in ChinaAvoid warningsHigh anonymityBypass locksFile sharing/TorrentsSecure data transmissionTOR (.onion) accessFirewall & Protection
The basic idea when the company was founded was to protect the users and the company.
The VPN service is provided via Panama and billed via Switzerland. This combination guarantees that there can be no connections between users’ payment data and user names or logs of activities. In addition, this already prevents users from being legally investigated. The Swiss company knows neither the end nor the user names and the company that runs the technical implementation do not know any billing data of the user. What is not known, no one can legally demand.
Many details, but still easy to use
In the following test report, we will describe many details of the service. We have tried to explain these details in a readable way, which means that we also want to simplify some of the details. Especially with rather complex technical services like Perfect Privacy, this is certainly helpful.
So simple: Simply connect Multihop (cascade)
Perfect Privacy advantages
Perfect Privacy is great for:
- Streaming and bypassing geographical barriers
- Secure use of file sharing/file exchanges
- Maximum anonymity on the Internet
- Secure data transmissions without log file storage
- Anonymous secure communication over the Internet
- Extended protection against attacks/hackers on own device/network
- Protection against any form of spying
- Protection against targeted surveillance
- Highest security standards on all devices
- Stable connections even in restrictive environments (corporate networks, China, etc.)
Confirmed security with Perfect-Privacy VPN
We visited the provider on 21.09.2021 in an office in Hamburg and were also able to get a personal impression of the operators. The operators are among the idealists in the field of data protection and have been involved in the Chaos Computer Club for many years, among other things. In addition, Perfect-Privacy deals transparently with all data and facts about the operators and also the technical conditions and has therefore also been awarded our Trust-Level Certificate. Perfect-Privacy thus fulfils all requirements to receive our recommendation for data protection and privacy.

The first personal interview with PerfectPrivacy VPN
We visited the provider and recorded a video of our conversation about the background of the company and the everyday life of “privacy activists” in more than 1h45min. We would be happy if it helps you to get to know the provider and the people behind it a little better. Because choosing a VPN service is a question of trust! The video is available in German now.


Perfect-Privacy VPN is classified as particularly trustworthy.
Our trust level: “100 per cent
The provider Perfect-Privacy VPN answered all our questions about the background of the service 100%. For this, we would like to mark the service with our “Trust Level”. Only a transparent approach to details about the company, the technology and the service deserves the trust of the users.
All answers from Perfect-Privacy VPN to our questions: Trust level
69 of 69 questions asked about the background of the company and the technology used were answered.
| Operating site | PanamaSwitzerland |
| Clearing location | Switzerland |
| Local legislation has an impact on customer protection | ✔ |
| Operation and billing separately | ✔ |
| Server locations | 25 |
| No log files | ✔ |
| Own DNS Server | ✔ |
| Virtual server | ✘ |
| Dedicated server | ✔ |
| RAM-Disk Server | ✔ |
| Hardware owner | ✔ |
| IP addresses owner | ✔ |
Perfect-Privacy has no speed limits
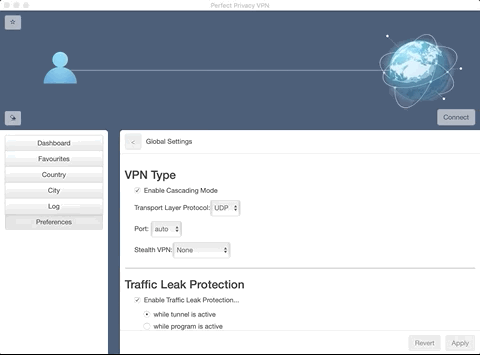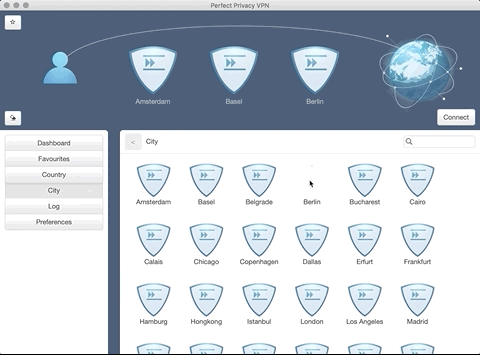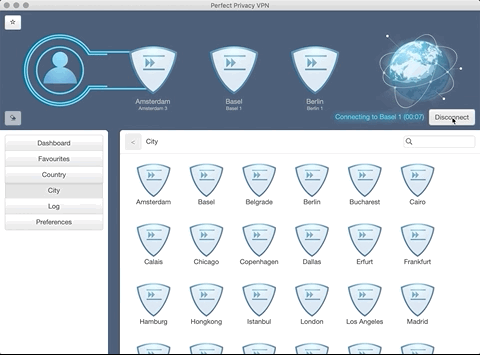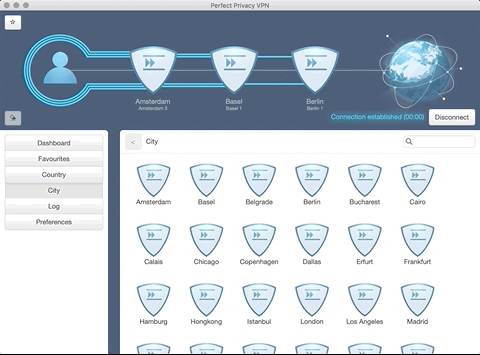
To avoid network bottlenecks, the load of the servers is monitored and new VPN servers are provided if necessary. The current server situation can be constantly monitored and controlled by the user on the website. The maximum encryption of the data requires a lot of resources.
If you notice a strong loss of speed when using Perfect-Privacy VPN, then the settings of the extensive possibilities have certainly not been made correctly. Most often the wrong protocol or encryption method is used, here alone the provider offers more than 10 different variants.
Therefore, UDP OpenVPN is the standard for most applications, but IPsec and also the OpenVPN variant with TCP configuration. However, you can get the maximum possible speed in any case.

Maximum speed via VPN
This means that the connection speed of the server is the limiting factor. For this factor to be transparent, the customer can view the availability and also utilisation in detail via the server status overview. As a rule, Perfect-Privacy expands the technical requirements already at an average utilisation of 20 %, which is why every user is guaranteed to be able to use the maximum transmission speeds.
More than 450MBit/s via VPN?
It is therefore not uncommon or impossible to achieve data speeds of more than 450MBit / s even with maximum encryption. In detail, the access to the Internet, the path via the Internet to the VPN server and also the own hardware are used. OpenVPN with 256-bit encryption is partly required for this kind of calculation of own hardware also at the VPN client.
The Perfect-Privacy Network
In our test report, Perfect Privacy provides servers in more than 25 different countries. The locations of the servers are distributed worldwide in such a way that it is possible to access a nearby location via an encrypted connection and also to get close to a target of the data query (web server or web services). The focus was not directly on IP addresses that are available to as many countries as possible, as these would also not affect the protection of the user.
Encrypted networked worldwide server landscape
The servers are linked to each other using VPN connections and only the data between the locations is transferred via these connections.
“Neurorouting” uses the potential of the network
In addition, this linking enables the servers to keep the time spent on data outside the Perfect Privacy network as short or as small as possible. This function, also known as “neurorouting”, was only made possible by constant networking. Likewise, the transmission speeds and also ping times are optimised as much as possible via the cascades. (A disadvantage that normal VPN cascades have for technical reasons).
Privacy with PP
Perfect Privacy delivers absolutely everything a user can expect in terms of privacy and even goes beyond that.
Anonymous on the Internet Changed virtual location ✔ Protection against requests for information ✔ Prevent general monitoring ✔ Prevent targeted surveillance ✔ No log files ✔ Obfusication (masking) ✔
Perfect Privacy for Download & Torrent
If you’re looking for a VPN service for torrents, Perfect-Privacy already has everything you could want. KillSwitch, WebRTC security, port forwarding, crazy fast servers etc. Simply everything you need for a worry-free torrent experience.
Get Perfect Privacy for Torrent now
Download and torrent Torrent use allowed ✔ Own Torrent Server ✔ Avoid warnings ✔ Port forwarding ✔
Perfect Privacy for Streaming
| Streaming of TV and video content | |
|---|---|
| Use on home router | ✔ |
| Use with KODI | ✘ |
| SmartDNS | ✘ |
| FireTV App | ✘ |
| Avoid warnings | ✔ |
| Supported international streaming platforms | Disney+ (US)Hulu (US)Amazon Prime Video (US)Netflix (US)Apple TV (US)Watch ESPN (US)Channel 4 (US)NFL Gamepass (US)MLB.tv (US)abc (US)CBS (US)FOX (US)NBC (US)Showtime (US)FLIX (US)epix (US)HBO Now (US)ITV (UK)Eurosport (UK)Sky (UK)BBC iPlayer (UK)Sky News (UK)Bloomberg (UK)BT Sport (UK)Channel 4 (UK)Sky Go (IT)YouTubeSpotifystarz (US)hustlerTV (US)PenthouseTV (US)PlayboyTV (US) |
Perfect-Privacy scope of functions
If you are a little cautious because you are looking at a long list, you should know that we have not even compiled everything here. Much will be explained later. Technically, Perfect Privacyis top-notch.
Special functions IPv4 ✔ IPv6 (new) ✔ Static IP ✔ Shared IP ✔ Multi-hop VPN ✔ NeuroRouting ✔ Malware filter ✔ Firewall ✔ Tracking Blocker ✔ Obfuscation (mask) ✔ RAM disk (k.HDD) ✔ AlwaysOn Server ✔ Own DNS ✔ Port forwarding ✔ VPN-to-TOR ✔ No log files ✔ Autom. IP change ✔ LoadBalancing ✔ Virtual server ✘ Dedicated server ✔ Own hardware ✔ Own IP addresses ✔ SmartDNS ✘ Own Torrent Server ✔ KillSwitch ✔
Available Locations
Perfect-Privacy Locations have been selected to provide fast and secure access to the PP network while bringing the secured network to data destinations (web servers).
Perfect Privacy servers are currently operational in the following countries:
Australia, Canada, China, Czech Republic, Denmark, France, Germany, Iceland, Israel, Italy, Japan, Latvia, Luxembourg, Netherlands, Norway, Romania, Russia, Serbia, Singapore, Sweden, Switzerland, Spain, Turkey, UK and USA.
However, more locations may be added in the future.
The exclusive functions of Perfect Privacy VPN
Multi-Hop and VPN Cascades
One of the essential security features of Perfect Privacy is VPN cascades also called Multi-Hop VPN. You can configure up to 4 locations in a row using the VPN client software for Windows or macOS. One’s data is transmitted via these selected locations in a multi-encrypted and untraceable form.
Purpose: Protection against targeted surveillance
This allows you to protect yourself from targeted surveillance by international organisations, but you can determine how your data is routed and also select the IP addresses that are then used.
Only very few VPN services offer this form of additional protection when using VPN; the statically set up routes of VPN cascades are also not comparable with this, as they would be predictable.
NeuroRouting from Perfect Privacy VPN
NeuroRouting ™ means that data traffic stays in the strongly encrypted VPN network as long as possible and always corresponds to the nearest VPN server. As a result, data traffic only appears on the Internet where it is needed. This process takes place dynamically and fully automatically as soon as one has activated this function in the customer area (for all devices, even manually configured ones, for example, smartphones, routers, etc.).
NeuroRouting ™ from Perfect Privacy offers the following advantages:
- Chooses the shortest but most secure path to the nearest VPN server.
- Data traffic remains in the encrypted VPN network as long as possible
- External VPN IP address changes depending on the destination
- Ideally, the data traffic does not appear on the Internet at all
- The number of attack points is greatly minimised
- Makes tracking much more difficult
- Dynamic: the algorithm “learns” and reacts to changes
Please note:
This is a security feature. It should not be used if the best possible download speed is required (e.g. for torrents) or if you want to always use a specific VPN location.
Get Perfect Privacy with Neurorouting now!

The Perfect Privacy Server concept is all temporary! (RAM Disk)
Perfect Privacy VPN Servers are not run on hard disks as usual, but directly and exclusively on temporary memory (RAM Disk). This means that data is always deleted. This concept reliably prevents that after a third party accesses the server (confiscation etc.) NO data can be recovered, even though elaborate technical possibilities. This protects the user from official access permanently. However, this requires a server with considerably more RAM.
Consistently secure.
However, no compromises are made in data security.
“Track-Stop” filter for harmful or monitored content!
With the “Track-Stop” filter function, Perfect Privacy is now suggested by its users and prevents, automatically and already on the servers, from loading harmful content. What is particularly good about this is that the individual filters can be switched on and also off manually. In addition to ad blockers, this also includes filters for all Google scripts and Facebook tracking codes. This means that you can be permanently monitored with just a few mouse clicks.
Function overview “Track-Stop”:
- Protection for children & young people (porn sites, violence, etc. are filtered)
- Protection against tracking cookies
- Protection against malware introduced via ad servers
- Protection against phishing sites
- Protection against tracking methods
- Blurs the line between browser use with and without VPN
- Surfing without advertising – without additional software
- Individually configurable (selection of several block lists)
More information about Perfect-Privacy “Track-Stop”
Absolute security and always without compromise!
Perfect Privacy VPN uncompromisingly uses all technical means to guarantee the user’s identity even in the case of forced attacks or even errors in operating systems or browsers. A good example of this is the use of a dedicated DNS server and active DNS leak protection. But also WebRTC Leak or other IP-Leaks have no chance with the Perfect Privacy Software. In combination with the technical possibilities, we know of no VPN provider that can guarantee data security on all devices. Users are therefore better protected than with any other provider and are always anonymous!
Full IPv6 support! (IPv6 Leak Protection)
Perfect-Privacy was the first provider to recently add IPv6 support to the service. This means that after establishing an OpenVPN or IPSec connection, users will automatically receive an IPv6 address in addition to the normal IPv4 address. This gives full access to the IPv6 network, even if your provider does not offer IPv6. In addition, this means that the IPv6 integration in the Perfect Privacy client is also automatically protected from IP leaks via IPv6.
No log files or records – at any time!
Furthermore, the VPN provider has equipped its servers in such a way that there are no records. Even current connections that run via the servers are not recorded and all data is exclusively in the “RAM” of the servers. This means that a server that is disconnected from the power supply (confiscation) immediately loses all its current data and no conclusions can be drawn about users.
Perfect-Privacy also enabled us to check the descriptions of your technology and confirm that no data is collected from a technical point of view! The provider has won our trust! In addition, it is technically completely impossible through Multi-hop VPN or Neurorouting ™ that someone or even Perfect-Privacy itself can deduce the real identity (IP) of the user.
Perfect-Privacy is incomparable so far!
So far, we have not noticed any similar technical range of functions with all VPNs. Yes, it’s true that if you only compare the number of active servers or the available IP addresses of a provider, Perfect-Privacy won’t come out on top.
But in the field of application, the Perfect Privacy user who wants to, it is about real security and this has nothing to do with the supposed number of servers. Since it is about the final security under all possible circumstances, which also takes into account targeted surveillance by international services.
17 Advantages of Perfect Privacy compared to other VPN services:
- No hard disk usage in the VPN servers (No data in case of official confiscation of the hardware).
- No log files or protocols about users or activities
- No limitation on usage or number of devices/connections per user
- Billing (Switzerland) and technical provision (Panama) of services are in separate companies and states (protection against official pressure)
- Manually selectable and also dynamic VPN cascades (Neurorouting)
- All VPN locations are connected and encrypted. Data of individual users can no longer be filtered.
- Own dedicated and powerful hardware with transparent free performance resources (server status overview)
- No third-party apps/software (also exclusively own developments)
- Filtering and prevention of “tracking” not by websites, in different levels (TrackStop)
- Disguising of data packets to protect against detection by the Internet access provider
- Adaptation of ports and transmission techniques to enable stable connections even in highly restrictive networks.
- Always constant IP addresses or also shared changing IP addresses are possible
- The use of IPv6 is natively supported (inbound and outbound) on all servers.
- Different types of port forwarding are configurable
- Direct access to the Onion network is possible (VPN to TOR)
- Widest choice of protocols: PPTP, IPsec, IEKv2, SSL, SSH, SSH2 and HTTP and SOCKS5 proxies are available.
- Widest choice of transmission methods:
OpenVPN over UDP (Layer 3) and TCP (Layer 2), as well as.
Stealth VPN SSH: OpenVPN profile for the use of an SSH tunnel (additional software)
Stealth VPN Obfsproxy: OpenVPN profile for use within an obfsproxy tunnel (additional software).
➡︎ Stealth VPN SOCKS: OpenVPN profile, for establishing a connection via ONE SOCKS proxy.
➡︎ Stealth VPN stunnel: OpenVPN profile use within a stunnel tunnel (additional software)
There are a large number of apparent technical differences compared to other providers.
These 17 points make the service unique in its entirety. Other VPN providers cannot offer more than 3 of these points.
During most of the own presentations, the technical features of Perfect Privacy become transparent and comprehensible.
The Perfect Privacy applications
You can use the service on any device, including Windows, macOS, Android, Apple iOS, Linux devices and of course routers. However, the developers of Perfect Privacy try not to create and make available any software or apps through third-party providers.
All variants offered are always purely self-developed, as this is the only way to exclude built-in backdoors.
Own apps without backdoors
Therefore, there are own apps for Windows, macOS, Linux and Android. For other devices, installation directly in the operating system is recommended. Just as there is generally no comprehensive manual for all conceivable scenarios, there is also a user forum or even remote support.
Available protocols L2TP/IPSecPPTPOpenVPN (UDP)OpenVPN (TCP)Own protocolMulti-hop VPNSSL/ProxyIKEv2SOCKS5 Own applications/apps AndroidOpenWRTASUSWRTOpenVPN UDPWindowsMac OSXApple iOSLinuxTomatoDD-WRTOther OS/Integration KillSwitch function ✔ Applications language GermanEnglish
However, because the instructions have already been created in a picture-book style, so to speak, we do without corresponding examples and link directly to the instructions menu on the website:
Perfect Privacy on the router
The service supports L2TP, various OpenVPN configurations and also the most common VPN routers.
Operation on VPN client router Use on routers ✔ Load Balancing ✔ Failure-free operation ✔ Own router application ✔ Compatible with ASUSGl-iNetDD-WRTTomatoVilfo Router
The service can be applied very easily to a wide range of VPN routers without any firmware adjustments. With the Vilfo router, we were even able to realise speeds of over 430MBit/s in our tests. However, since Perfect Privacy provides many functions directly via its network, the combination of router + Perfect Privacy is also a very good and usable solution for many families and home networks, where all existing devices are more than adequately protected against threats.
Perfect Privacy is not cheap!
The service uses most of its revenue to improve its technology, not for marketing and commissions like many other VPN providers.
Expensive hardware and operation
You also have to know that you can of course rent and operate a VPN server for as little as 5 euros a month. However, this will certainly be based on a system in which hundreds of individual servers run virtually on one hardware. Perfect-Privacy promises, however, to do without hard drives and all third-party providers that could also record the user’s activities. Therefore, dedicated server systems with full access to the hardware must also be used. However, these naturally cost considerably more and can hardly be operated for less than 1000 euros a month.
The manual effort required by the functions is enormous.
Those who can maintain or set up servers automatically save on maintenance and operation. However, automation is not possible with the solutions developed by Perfect-Privacy itself. The omission of protocols for monitoring the server is also given because the technical team of Perfect Privacy is more than well utilised. Of course, an increased effort for specialists is also reflected in the operating costs.
The small target group of users
In addition, a service like Perfect-Privacy is aimed at a small group of people with a special need for their digital security. Therefore, unlike other “marketing-oriented VPNs”, Perfect Privacy has a much smaller user base.
Every customer can use Perfect-Privacy on an unlimited number of devices at the same time and regardless of location!
Costs / Tariffs Free use ✘ Tariff (1 Month ) 12.99 EUR Tariff (12 Months ) 119.99 EUR (per month 10 EUR) Tariff (24 Months ) 214.95 EUR (per month 8.96 EUR) Number of simultaneous connections per account unlimited Test options Money-back guaranteeLimited free trial time (Without payment)
General conditions:
- There are no limits on the amount of data, no restrictions on use and the service can therefore be used on an unlimited number of devices at the same time and from different locations.
- This also includes personal assistance with questions or problems as well as all available services, functions and applications.
- There is no automatic or recurring debit and the user manually opts to renew the service after the prepaid period has expired. NO CONTRACT.
Outstanding customer service included
PP’s customer service can be reached via e-mail at any time, even 24 hours a day, and responds very quickly. The technicians also help via TeamViewer and only give up when all problems have been solved, the user is satisfied and can use the internet via the VPN.
Customer service Applications language GermanEnglish Customer service ForumFAQ website Language in customer service GermanEnglish
Conclusion:
“Perfect Privacy” – as if the name said it all. The provider is based in Switzerland and goes to enormous lengths to keep its users anonymous. Even government enquiries cannot be answered. Absolutely recommendable when it comes to your own privacy. Perfect Privacy is in the more expensive premium segment, but the few euros more per month are certainly worth it. Because you get a VPN provider you can really trust!
Erstellt am: 11. July 2022

