Table of Contents
Multi-Hop: Cascading VPN connections
Multihop are multiple encrypted connections with multiple identity changes that disguise the anonymity of the user.
It is simply connecting from one location to another via VPN, but the VPN provider must explicitly support and allow this. A HOP (telecommunications) is the path from one device or server to another.
“Multi-hop”, therefore, is a connection “made in series” on more than one hop/server/device.

The purpose of VPN cascades (VPN cascading):
Improved disguise and less information in server log files
The advantage is significantly improved hiding of the starting points of your data, as well as the fact that no server has a sender + receiver. Thus, on no VPN server, in the cascade “sender + destination” are known at the same time. Even log files cannot provide evidence of the transfer of particular data.
Explanation of different VPN connection types
Simple VPN connection
With a simple VPN connection, an encrypted data connection is established between the VPN client (user) and the VPN server (VPN service). The user then uses the IP address of the VPN service for his or her activities on the internet.
The user’s Internet service provider sees the data connection between the user and the VPN server, but cannot see what content this data is transporting.

✔︎ Simple VPN connections are the standard functionality of all VPN providers.
Simple cascaded VPN connection (DoubleVPN)
With a simple VPN cascading, the VPN server establishes another connection to another VPN server. The user’s data, therefore, leave a different server than the one to which the user has connected. However, since the paths of the data are mostly predetermined, internationally operating services may be able to anticipate them. But it is still a vast improvement over “simple VPN connections”.
In this case, the internet provider can also ONLY recognise the first data connection, without being able to recognise the transported content. However, it cannot trace which server is used to use the internet.

✔︎ Einfache VPN-Kaskaden, sind derzeit auch bei OVPN, NordVPN, VPN.ac, und Perfect-Privacy VPN verfügbar.
Multiple cascaded VPN connections (multi-hop VPN)
With multiple VPN cascading, the user can decide for himself which paths and via how many VPN servers his data should be routed. This means that the predictability of data forwarding is significantly lower and therefore also significantly more difficult or impossible to monitor.
In this case, the internet provider can also ONLY recognise the first data connection, without being able to recognise the transported content. However, it cannot trace which server is used to use the internet.
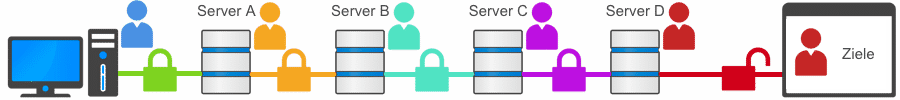
✔︎ Multiple individual VPN cascades, are currently only available with and Perfect-Privacy VPN.
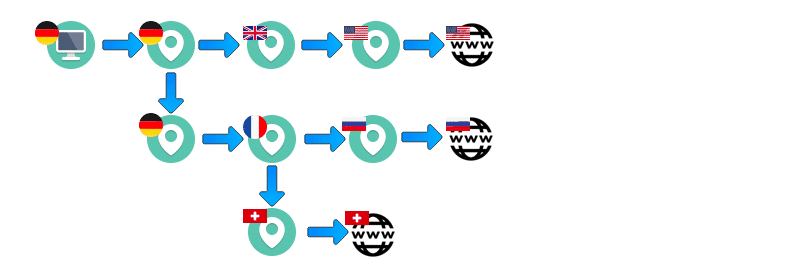
Multiple dynamic cascaded VPN connections (neurorouting)
VPN Cascading – multiple dynamic connections
With neurorouting from Perfect-Privacy VPN, the data is routed differently and dynamically over the own VPN server network depending on the destination. The focus here is that the data reaches the destgoalsredictably and individually on the one hand and also remains in the secured network over the maximum possible path to the destination. This makes monitoring impossible due to the dynamics of the system and also reduces the risk of the last unencrypted path from the VPN outgoing server to the destination by selecting it automatically.
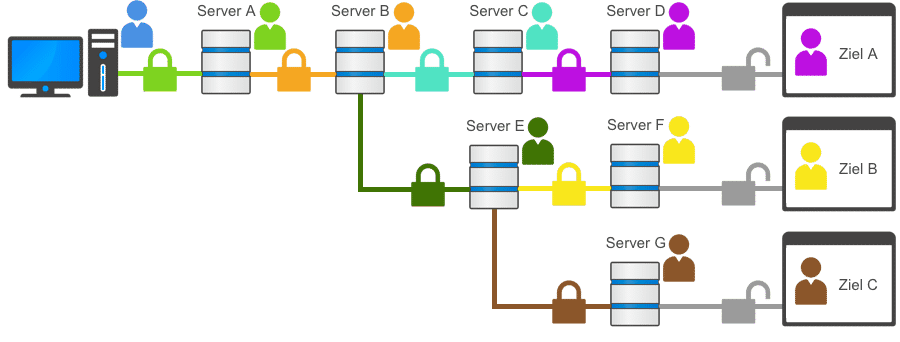
✔︎ Neurorouting is currently only available with Perfect-Privacy VPN.
WARNING: Interleaved VPN connections are not “cascades”.
Anyone who creates two or more interleaved VPN connections is committing several gross and negligent planning errors, which will in no way lead to improved measures against surveillance!
Common attack scenario to expose users of Interleaved VPN connections
Interleaved connections can always be attacked by targeted measures, whereby the outer VPN connection is deliberately brought down using “data injecting”. The consequence is that the IP address of the inner VPN connection changes and this inevitably collapses. As a result, a kill switch or other protective measures are ineffective for a few seconds, as an attempt is made to automatically establish a new connection. The real IP address of the user can then be determined very easily. The user can even remain unaware of this.
Two VPN connections to each other can always be unstable
This is because the headers of the data packets have to be read out differently in the case of interleaved connections, which means a significant additional effort for the VPN servers. But also by manipulating the headers of the data packets, recognisable facts are created which can provoke the blocking of these data by routers in the network. Both lead to the fact that interleaved VPN connections usually cannot run stably in the long term. Short failures are usually not noticed by the users, but lead to the publication of one’s own identity on the Internet.
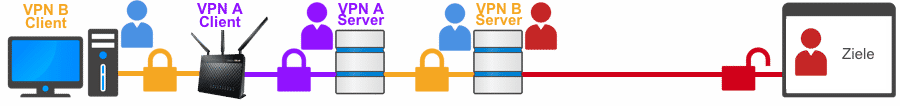
If I may give you some advice, don’t try to improve your security with interleaved connections. In the end, you will achieve the exact opposite. A simple VPN connection is preferable to a “interleaved double connection” in any case!
“Multi-Hop VPN” is thus the only technical solution that enables the following three security aspects
- No VPN server used processes/stores the data necessary for exploration (origin<>destination).
- A possible logging/logfile storage of the VPN servers would thereby NOT be able to reveal any clues to “user <> activities”.
- Even if targeted longer-term monitoring, even of the servers in general, takes place, this makes it completely impossible to track user activities.
Hint:
With the “conventional VPN connection type (1 x device to 1 x VPN server location), it would theoretically always be possible to log the use of the VPN server and all logged-in users or possibly also specifically track individual user activities. Likewise, it would be possible to record and store all incoming and outgoing connections of a VPN server evenwithout direct accessN server logs (log files) could also have logged individual users or their activities. These risks can only be eliminated by multi-hop VPN.
An example of a VPN cascading:
The user logs on to a VPN server in Switzerland. He is assigned a Swiss IP address there and the channel between the user and the VPN server is encrypted with OpenVPN and 256-bit. From there, the user initiates a connection to a VPN server in Russia with his “Swiss identity”. He also establishes an encrypted connection and is assigned a Russian IP address, then the user logs on to a VPN server in Brazil using this…etc.
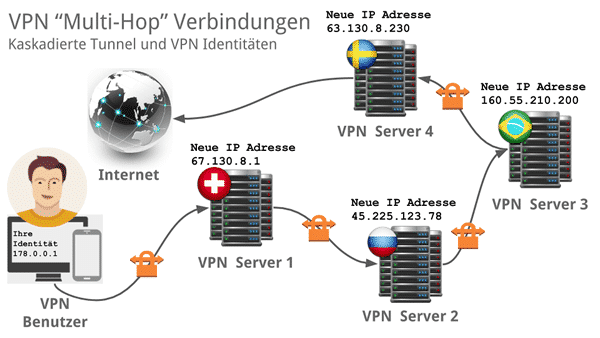
Basically, the original data traffic is encrypted and interleaved up to 5 times and the identity is changed and disguised just as often on the way to the destination on the Internet. This also means that the second VPN server only receives the identification data of the previous server and is no longer able to deduce the actual identity of the user.
Why is a VPN cascade more secure?
A server or router always sees the IP address of the device that connects to it and where it forwards data to. This means that a VPN server knows the real IP address of the user and also where it sends the data.
In a cascade, the first VPN server sees what the real IP address is, but it only forwards it to another VPN server. It therefore no longer knows where the target data will end up. The second VPN server also only recognises the last IP address and thus only that of the first VPN server. This server therefore no longer has any information about the real IP address of the user.
If one of these VPN servers is fully monitored, then the overview thatined is never complete! Either the destination or the origin is always missing. Therefore, cascades of VPN servers are the safest method to avoid targeted surveillance.
Consequently, from 2+ servers (i.e. at least 3), the possibility of obtaining an overall picture is mathematically equal to “ZERO”. A VPN cascading of 3 or more VPN servers is therefore the highest level of security against traceability.
The TOR/Onion network is similarly structured
The providers Perfect-Privacy VPN and NordVPN from our test also offer this in an even more complex way. In addition to the multiple interleaving, you can also set up a TOR connection using the provider’s technology, which results in the identity being disguised 4-5 times again. The entire TOR network is built based on multi-hop, but in the TOR network, one cannot predetermine an endpoint and has no control over the possible routes. In addition, most TOR servers are of course privately operated and therefore have limited bandwidth and performance.
Multi-hop VPN provider:
No other technology offers more protection of anonymity!
In general, with every multi-hop connection, reduced bandwidths must of course be expected due to the multiple encryptions and also the longer distances. Perfect-Privacy nevertheless offers acceptable services, especially in comparison to TOR. The reason for this is that the provider uses special servers for this purpose and provides the corresponding bandwidths.
In our entire test, only a few providers currently offer this technology > Perfect-Privacy VPN, ZorroVPN (does not exist anymore) and NordVPN (limited to fixed routes), but there are also a few others.
VPN cascading: the cascades are secure, and dynamic cascades are even better!
NeuroRouting™ from Perfect-Privacy VPN
NeuroRouting™ is the name Perfect-Privacy VPN has given to its latest innovation, which also relies on VPN cascading, but aligns them dynamically and according to the destination. This all happens fully automatically and the system is also constantly learning, making it ever more secure and faster. It is impossible to predict which router the user will use to send or receive the next data, and the data is routed as far as possible in the secure Perfect Privacy VPN network. This significantly reduces the risk of tracking by international surveillance measures, prevents an attack on encryption techniques and incomparably anonymises the users!
NeuroRouting™ with dynamic VPN cascading depending on the destination address (on the Internet)
End device ➩ VPN server 1 ➩ dynamically selected VPN server 2 ➩ dynamically selected VPN server 3 ➩ Destination address on the Internet
| Provider | Evaluation | Privacy | Price | Links | |
|---|---|---|---|---|---|
 | Perfect Privacy VPN |
| from 8.96 EUR | Website Website Review | |
 | Surfshark VPN |
| from 2.19 EUR | Website Review | |
 | OVPN |
| from 4.22 EUR | Website Review | |
 | NordVPN |
| from 3.39 EUR | Website Review | |
 | vpn.ac |
| from 3.75 USD | Website Review | |
 | Private Internet Access |
| from 1.79 EUR | Website Review |
Erstellt am: 28. October 2022
